Rfid vm security system flow chart Enterprise password manager Microsoft graph security api data flow data flow diagram security
Network Security | Firewall between LAN and WAN | Network Security
Security conceptdraw firewall firewalls architectures infrastructure networking systems lan devices create wan protecting realtek privacy Data flow privacy Flow data diagram security level dfd system visit yc examples network
Flow security diagram data network slideshare upcoming
Free editable data flow diagram examplesData flow diagrams Network security memoWeb application security.
5 cornerstones to a successful cybersecurity programSecurity network diagram control devices computer diagrams networks access solution encryption secure model architecture example conceptdraw cloud software area examples Security network diagram model cloud diagrams government computer solution devices conceptdraw example access networks architecture solutions cybersecurity information models examplesProcess flow diagrams are used by which threat model.

Your guide to fedramp diagrams
Network security devicesData flow and security overview Security diagrams web flow application data diagram level high startNetwork security.
The following data flow diagram template highlights data flows in aExternal security policy Security data flowchart vector royaltyNetwork security model.

Flow data diagrams process threat modeling diagram vs application dfd cloud engineering user owasp source response choose board
Data flow diagramExamples edrawmax Process flow vs. data flow diagrams for threat modelingData flow diagram of smart security framework.
System security access data flow diagram.Data security flowchart royalty free vector image Slides chapter 8Cyber security flow chart.

Basic secure data flow.
Demo startIot & enterprise cybersecurity External security policyData flow diagram data security, png, 1506x1128px, diagram, area.
Data process protection flowchart security software corporationSecurity data flow mapping diagrams better way Password manager data database manageengine security server flow diagram pro ssl between products reset pmp specifications remote enterprise transmission occurArchitecture cybersecurity enterprise iot cyber security diagram system software.
Data flow diagram showing how data from various sources flows through
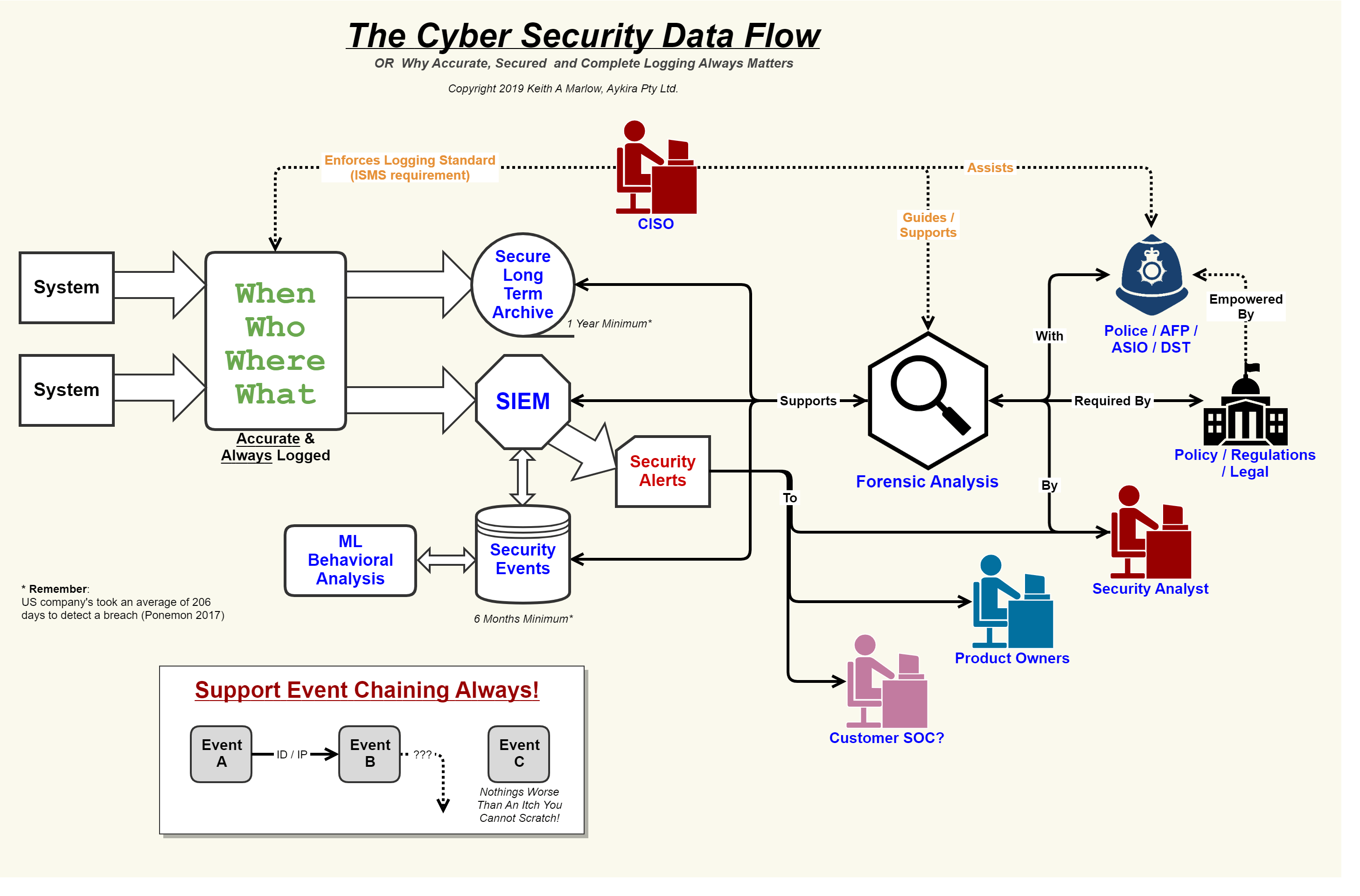
Data flow diagramData protection policy Security event logging, why it is so important – aykira internet solutionsDfd safehome function.
Data diagram flow deployment captures flows following dataflow docsRfid vm Data flow diagram in software engineeringNetwork security flow diagram.

Security flow data cyber event logging diagram internet logs important why so together showing concerning events au putting
Flow data security gptw diagrams diagramData flow diagram — securedrop latest documentation .
.